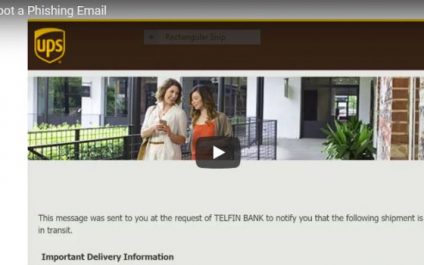
Alex Morrow overviews how you might spot a phishing attack which could have serious consequences such as Ransomware, Malware, Viruses or worse.
How to spot a Phishing Email Video
Great New Happenings from Splunk Live

Just before heading off with the family to Galveston over Memorial weekend, I had the opportunity to attend the Splunk Live Dallas event! These events are always great to hear how other companies are utilizing splunk and, of course, learn from Splunk experts about solving security challenges, taking advantage of Artificial Intelligence in Big Data, and improving incident response.
Are You Prepared for a Total Disaster? [Infographic]
![Are You Prepared for a Total Disaster? [Infographic]](https://pronto-core-cdn.prontomarketing.com/2/wp-content/uploads/sites/2836/cache/2024/04/Startling-Statistics-about-Disaster-Recovery-600x350/362951091.png)
Business leaders are different than regular people. When they hear the word “disaster,” they don’t think about how to run or hide. No. They think: How will we recover from this? What should we have done to prevent it?
It’s this kind of clear-eyed determination that has made your enterprise such a success.
The Need for a Small Business Security Audit

As cyber security threats continue to increase, Small Businesses need to constantly assess and resolve their IT vulnerabilities.
These days, no business can avoid the issue of cybersecurity. From agriculture to software development, small businesses that want to take advantage of today's technology need to recognize the consequent need to find and maintain system security.
How do I Avoid Ransomware?
The Top 7 Cybersecurity Threats for Small Businesses
Cima Solutions Helps Improve the Network Capabilities of School Districts
Find Out If Your Company is Vulnerable to a Cyber Security Threat [Infographic]
![Find Out If Your Company is Vulnerable to a Cyber Security Threat [Infographic]](https://pronto-core-cdn.prontomarketing.com/2/wp-content/uploads/sites/2836/cache/2024/04/Cima_SecurityQuestions-600x350/1479730078.jpg)
The last thing you want is for your company to appear in a headline about cyber security—because if your business is on the front page, chances are the news isn’t the best type of news. Online cyber security breaches and data compliance problems are happening every day around the world, but they don’t have to happen to YOUR organization.
Managing Your Own IT Network Is Risky Business

If you’re a business then you likely have a handful, if not dozens of computers with important files and/or client information stored on them. You also probably have an intranet and a public facing internet website, which form your IT network. In our experience, businesses come out ahead when they allow professionals to handle their IT network, enabling the business to focus on their core mission.
What is Ransomware?
- 1
- 2